
Secure remote updating of IoT devices without compromising on their operation
A remote updating system can be used to not only update but also manage terminal devices in a flexible, scalable and secure way. What should be taken into account in the update process?
In a conventional IoT system, most functions can be available in a cloud service, making the installation of updates very simple. However, with more complex IoT systems and higher number of terminal devices, update management and the update process itself becomes more complicated.
In an edge computing system, more and more computing power and other functions have been transferred for the IoT terminal devices to perform. This may be a system that utilizes machine learning directly on the terminal device. A system like this is more complex and decentralized than a similar system built on a centralized service.
What if the update fails?
The greatest challenges with remotely updated IoT systems concern disruptions caused by failed installations. This could be triggered by a power cut during the update, for example. However, even if the update has been successfully performed, it does not guarantee that the software will work without any faults. In the worst-case scenario, the device may be stuck in a state from which it cannot recover to be fully functional without assistance.
Other challenges with remote updates include limited access to the content of updates. In edge computing type of systems, such content may be a machine learning model used on the terminal device that is not to be shared publicly. The device to be updated must be able to ensure that the update has been sent from a reliable source, and the update system must also work together with disk encryption, if applied.
The update implementation depends on how extensively the software on the device must be modified. Updating a single piece of software is more simple than an entire operating system. If the update tool does not touch the device’s operating system or the piece of software that retrieves updates, a failed update will not compromise their operation. In case of a failed update, the update package can be either retrieved again, or you can wait for the next update that includes a correction package.
Updating an entire operating system may compromise the operation of the entire device. For example, a failed update of a Linux kernel or a client used for the installation may cause the device to be become so seriously jammed that it cannot recover without assistance.
Secure operating system updates
The most common solution for a secure operating system update on an IoT device is to have two parallel OS installations on different partitions. The bootloader keeps a record of an active installation and starts up the operating system from the partition containing it. When the operating system is updated, the new system is installed on the partition that is currently not used.
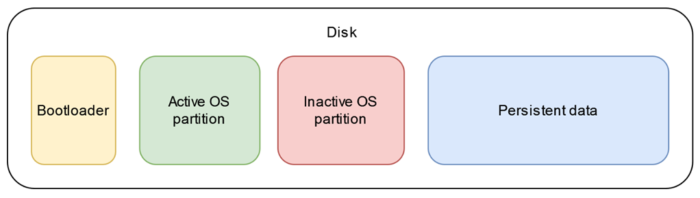
When the device is restarted, the bootloader attempts to download the OS from the partition that contains the updates. The OS installation preceding the updates remains operational and can be fallen back on if it turns out that the updated system does not function properly.
There are some tools available, such as Mender, BalenaOS and SWUpdate, to implement the solution described above. Most of the tools used are integrated into a tailored Linux distribution created with the Yocto Project. Yocto can build a minimalistic Linux-based operating system that includes the necessary dependencies and utilities in modular fashion.
IoT update tool suitable for production
An IoT device prototype that supports operating system updates is not suitable as such for production. The greatest shortcoming concerns security. The most commonly used tools for dual operating system installation do not support disk encryption, for example. Some of the tools also depend to a great extent on the service provider in terms of the availability of operating system updates, for example.
In terms of the work required for implementation, an IoT update tool suitable for production is probably somewhere between the extremes presented in this text. For example, tools utilizing Docker, such as AWS Greengrass, can be used to implement a system in which updates can modify the system extensively by means of containers. The software that installs the device’s operating system and updates can nevertheless be left intact. Security features, such as disk encryption, are easier to add to the system if the encryption management is not performed by the software that installs the updates.

Milan Mäkipää
Software Developer
I work as a software developer in industrial customer projects. I joined Atostek in 2019 while still studying. I am currently particularly interested in the software development of IoT systems and mobile applications.